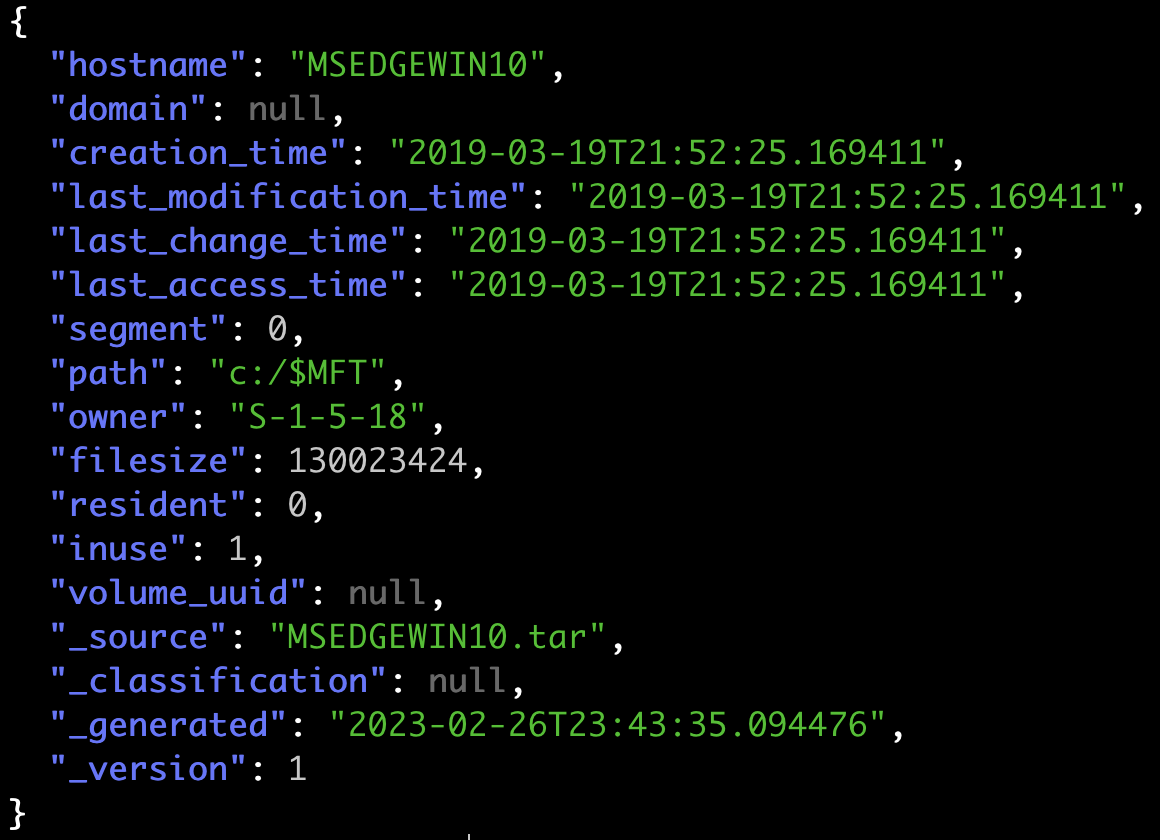
Vulnerability Disclosure
Recently, I got a question from a young hacker about how to start with Responsible Disclosures. This is a tutorial to contribute to the online Security of The Dutch Government. For the rules, see the guideline and the Coordinated Vulnerability Disclosure brochure. Please, before you start hunting read the rules!
Recon
Before hunting, you need a scope. I made a copy of The Dutch Governments web register and extracted all the URLs. The file contains 1189 domains. I would recommend you to execute a sub-domain scan so that you can expand your scope. For that, you could use tools like Amass, Subfinder, Aquatone or MassDNS.
Now you can start looking for vulnerabilities in the websites discovered from the sub-domain scans. For this, I use the OWASP Testing Checklist. Just follow the checklist, look for vulnerabilities and be creative!
Reporting
Now that you have found some vulnerabilities, you must explain them clearly so that the NCSC understands your report. For that, I recommend reading ‘Writing Reports’ from EdOverflow. Remember that the response time when reporting vulnerabilities is usually not so fast.
Own experience
The t-shirt below was the first reward I got for reporting vulnerabilities at The Dutch Government after a week of hunting. In the meantime, I have found dozens of vulnerabilities in the websites of The Dutch Government and received a lot of t-shirts for it. It is a perfect way of learning web vulnerabilities to become a web application pentester.