Malware Challenges Analyzeme No1
I saw this tweet about a RE challenge and thought why not just do it.
Fun little RE challenge by @danusminimus https://t.co/MfBOreSiZS
— Myrtus (@Myrtus0x0) May 3, 2020
Opening the executable in Ghidra shows the entry function that calls main.
int entry(void)
{
[...]
exit_code_main = main();
[...]
exit(exit_code_main);
}
The main function calls FUN_00401020(0x2d,100,10).
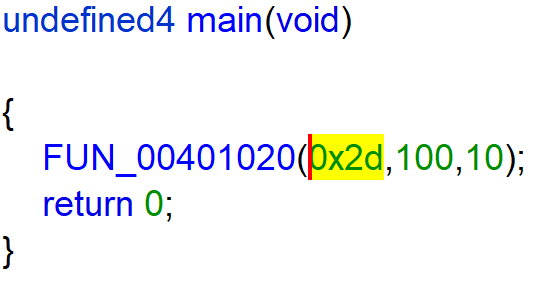
The function FUN_00401020 calls itself 9 times until it calls FUN_00401070.
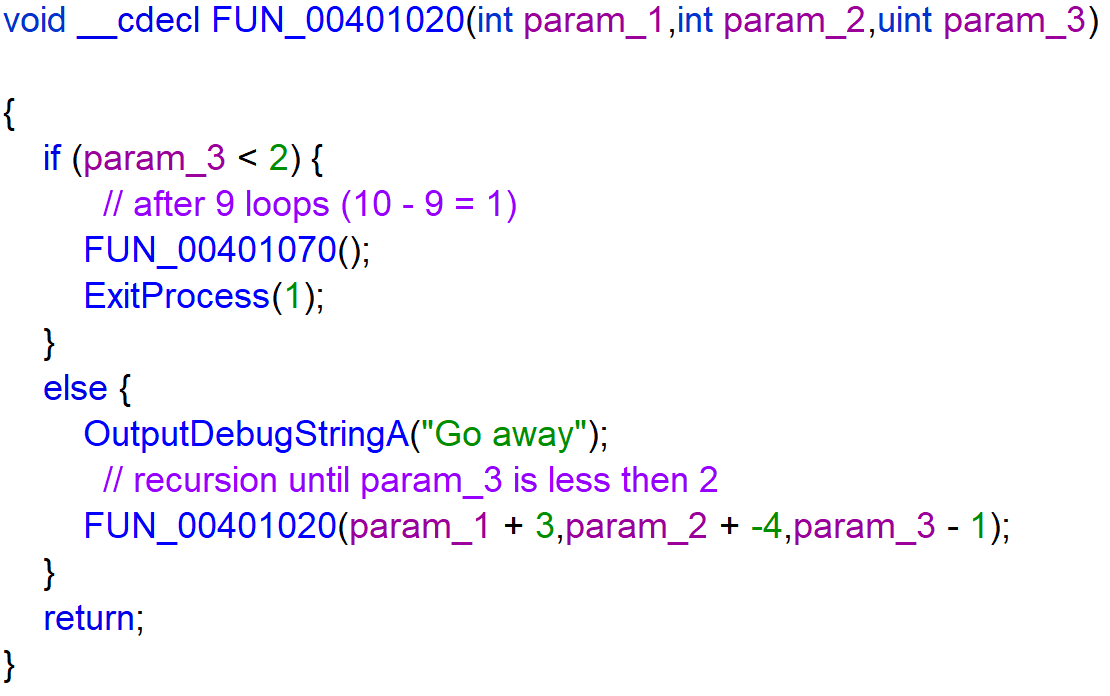
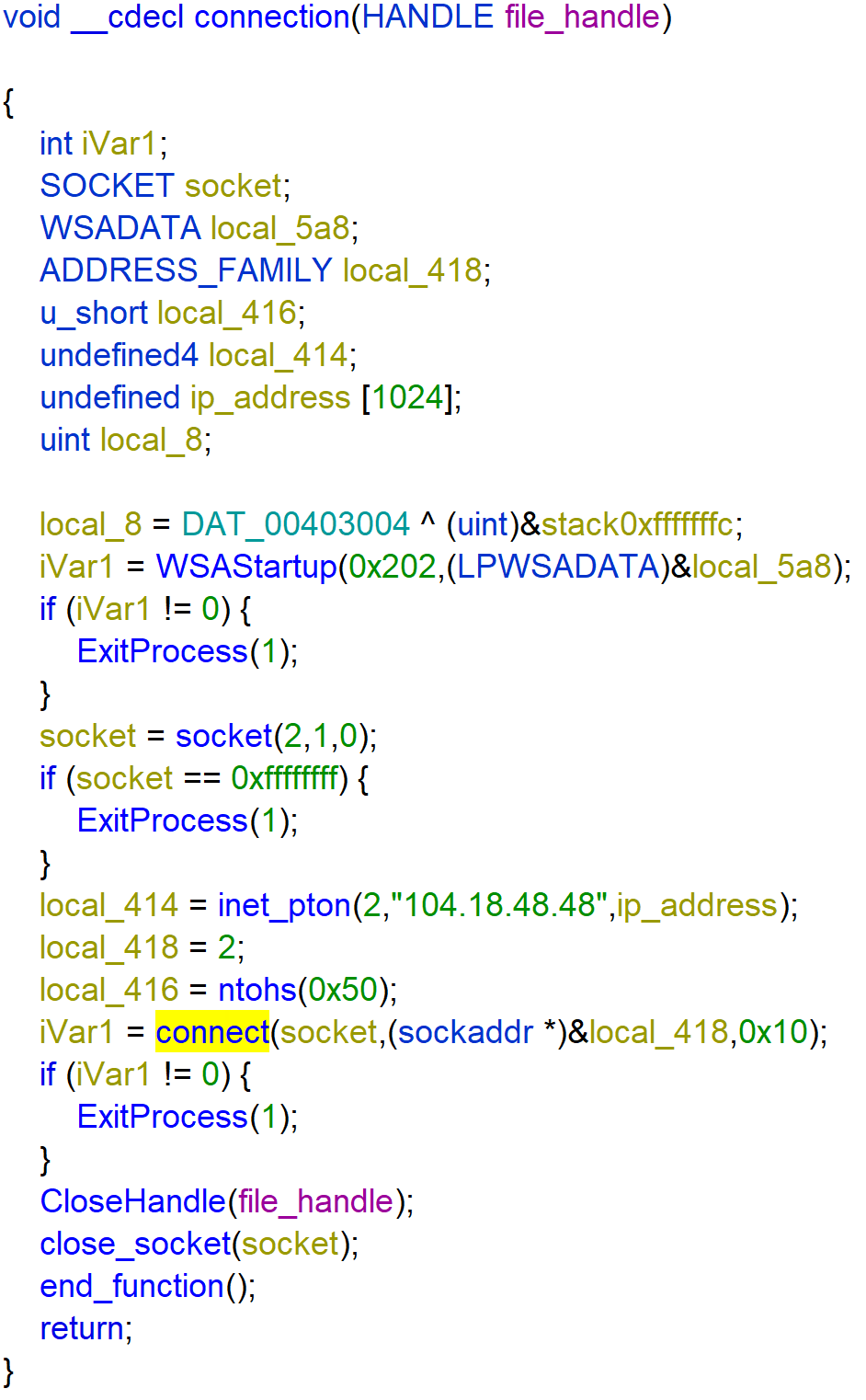
The function FUN_00401070 retrieves the temporary folder with use of GetTempPathW.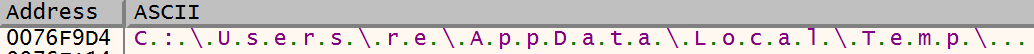
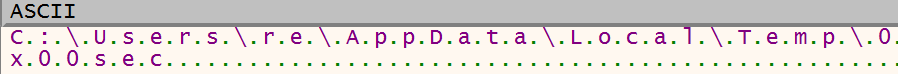
Then it appends the string 0x00sec to temporary path with use of wscat_s. C:\Users\re\AppData\Local\Temp\0x00sec
Then the function calls FUN_00401290 with temporary_path as parameter.
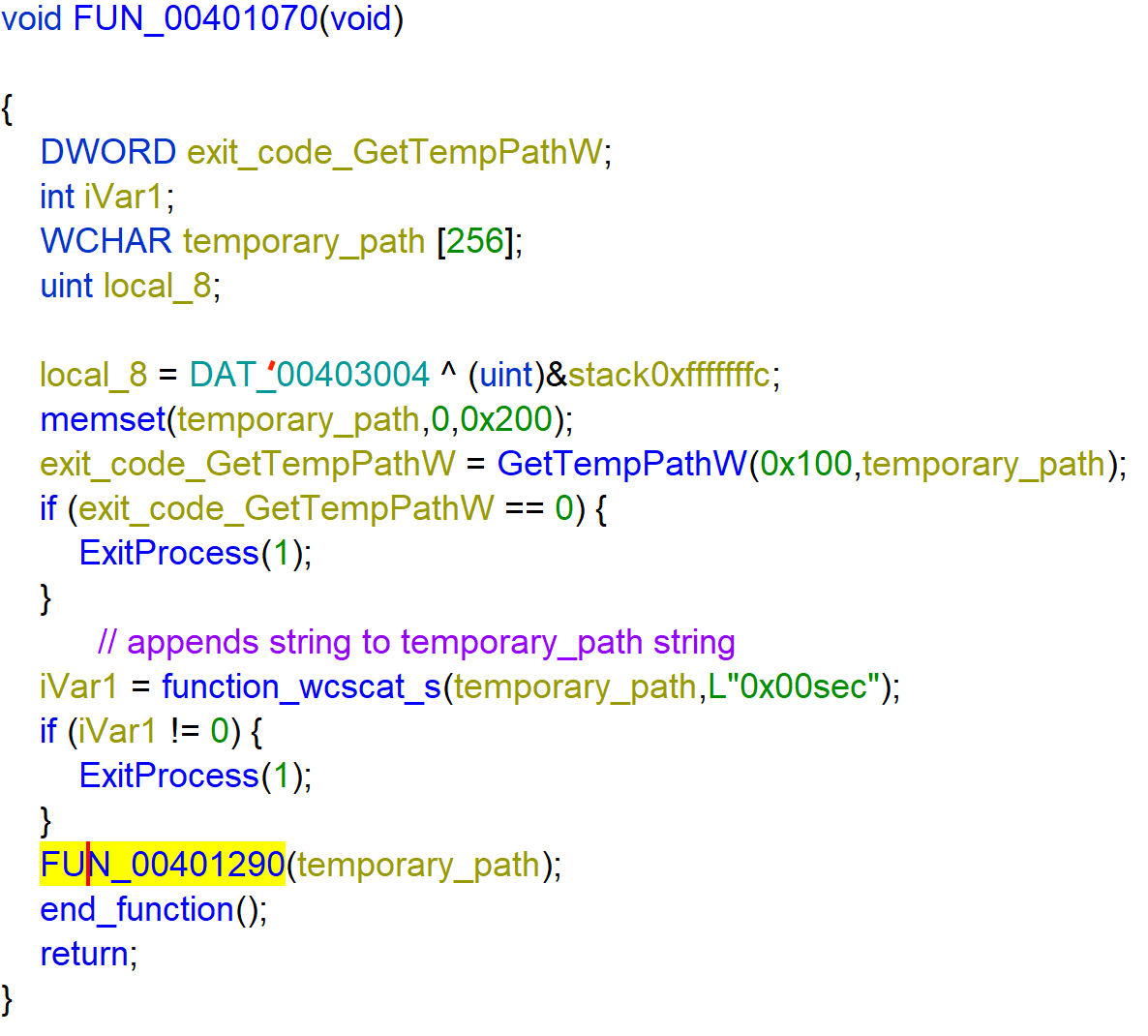
Creates a file at the path of temporary_path and calls FUN_00401110 with the file_handle. But if the file already exists it returns 0xffffffff and exits the process.
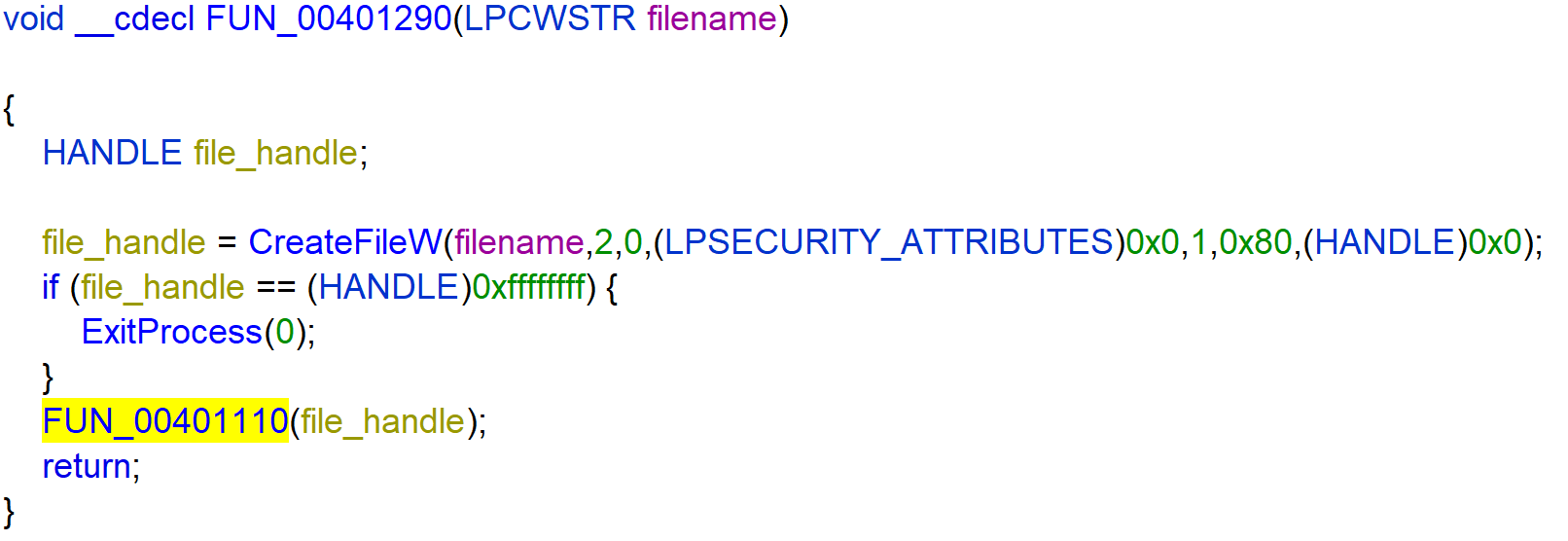
The function FUN_00401110 writes the string Greetings from nullsec! to the file_handle. And calls connection.
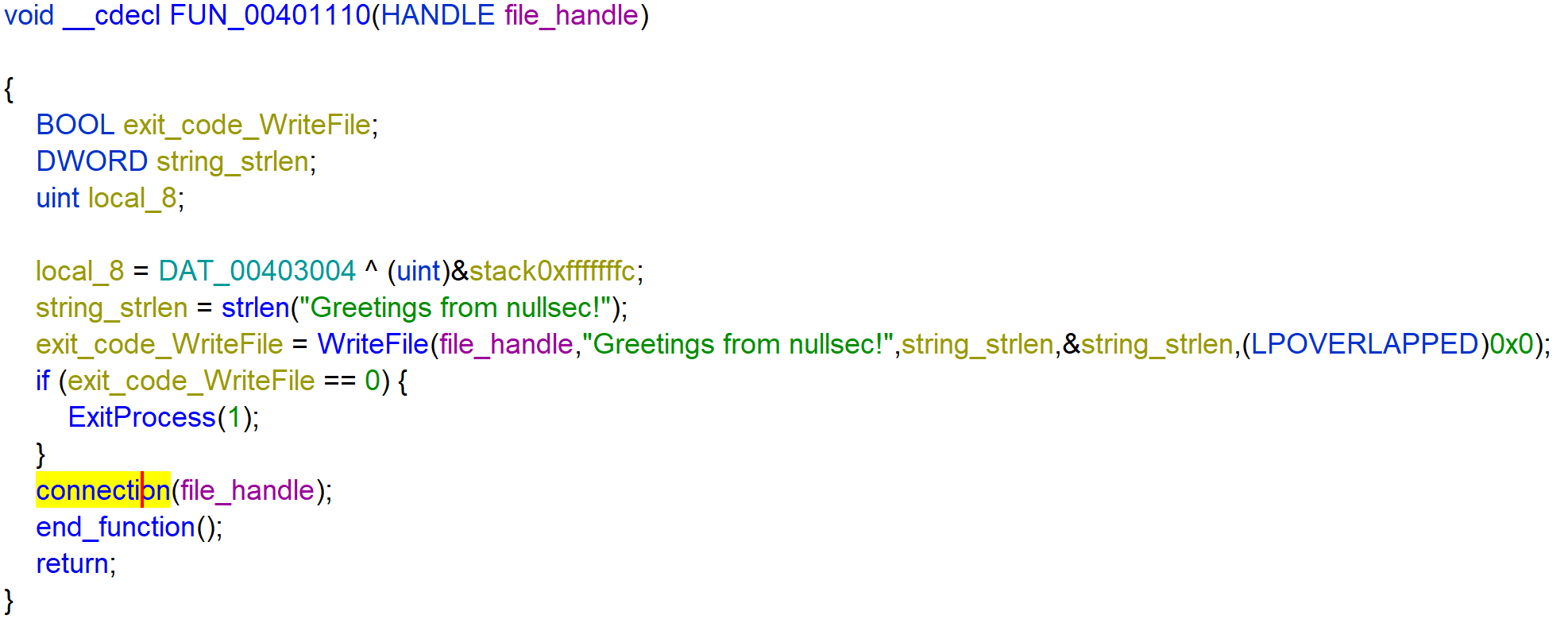
It creates a socket and uses the socket to connect to local_418. local_418 is a sockaddr structure where the address points to 1.0.0.0. This makes a connection to 1.0.0.0 over HTTP.

Technical assignment
The challenge also provided some questions about the malware sample answered below.
You must do the following tasks and please be verbose as possible:
Extract any host based indicators
-
Does the sample drop any files on disk? If yes where?
Yes it drops the file
C:\Users\re\AppData\Local\Temp\0x00sec. -
If a file is dropped, what is the contents of it?
The content is the string
Greetings from nullsec!.
Anti RE
-
How does the sample manage to “waste” debugging time? (Use a debugger for this one)
I don’t know maybe the recursion in the function
FUN_00401020.
Extract any network based indicators
-
Does this sample connect to any website? if it does what is the host name of that website?
Yes
1.0.0.0